Keep Your Crypto Safe: Essential Security Tips for New Aussie Investors
2023-10-06 11:28:05
Understanding Cryptocurrency and its Security Challenges in Australia
In the expansive realm of digital finance, cryptocurrency stands out as a revolutionary paradigm to redefine our understanding of money and transactions. Yet, as with any groundbreaking innovation, the rise of cryptocurrencies like Bitcoin, Ethereum, and numerous others, also comes coupled with a host of security challenges. From wallet protection to transaction integrity, the cryptosphere is a complex maze, demanding both understanding and vigilance from its participants. As the crypto-landscape continues to evolve at a breakneck pace, let's delve into its security aspects and understand what's at stake for investors in Australia.
The Basics of Crypto Security
Cryptocurrency operates in a decentralized framework, utilizing blockchain technology to maintain its integrity. At its core, crypto security involves two principal components: the cryptographic security of transactions and the secure storage of cryptographic keys. A user's private key is akin to a digital signature; it’s a proof of ownership and is used to sign transactions. Safeguarding this key is imperative, as loss or theft can result in the irrevocable loss of funds. On the other hand, public keys allow others to send you cryptocurrency, acting like an address in the crypto realm. Understanding the symbiotic relationship between these keys and employing secure wallets, both hardware and software-based, forms the foundation of crypto security.
Risks Associated with Crypto Investment
Cryptocurrency, for all its innovative allure, is not without its risks. Firstly, the market is notorious for its volatility. Dramatic price swings can happen within short timeframes, influenced by factors ranging from regulatory news to large-scale trading actions. Moreover, the decentralized nature, while liberating, lacks the traditional safeguards present in centralized financial systems. Phishing attacks, wherein attackers dupe individuals into revealing their private keys, are all too common. Additionally, given the irreversibility of crypto transactions, a mistaken transaction could mean permanent loss.
Why Crypto Security is Crucial for New Investors in Australia?
For new Australian investors treading the waters of cryptocurrency, security is very important. While the potential for high returns may be alluring, the nascent and complex nature of the crypto ecosystem can be a breeding ground for mistakes and oversights. With a lack of standardized regulatory oversight and the permanent nature of transactions, one misstep can be costly. Ensuring robust security practices from the outset can prevent devastating losses and build confidence in the investment journey. New Aussie investors, often unaware of the intricacies of the crypto world, can become easy prey for scams and frauds. Educating oneself about best practices, employing secure wallets, and being vigilant against potential threats are essential steps in safeguarding one's investments in this brave new world of finance.
6 Crypto Security Tips For Securing Your Bitcoin and Crypto Wallets (Updated 2024)
In the rapidly evolving world of cryptocurrency, where financial sovereignty and cutting-edge technology converge, the security of one's digital assets is paramount. As Bitcoin and other cryptocurrencies continue to gain widespread adoption and their value soars, so does the allure for malicious actors to exploit weak points in the crypto ecosystem. However, with the right knowledge and precautions, users in Australia can drastically reduce the chances of falling victim to potential threats. This comprehensive guide aims to equip readers with six vital security tips for safeguarding their Bitcoin and other crypto wallets from cyber adversaries.

Choosing a Secure Wallet
The first step in ensuring the safety of your digital assets is selecting a robust and secure wallet. This is the digital vault where your cryptocurrencies will reside, and its integrity is as vital as the security of a traditional bank account, if not more. Various factors come into play when choosing a wallet, from understanding its operational mechanisms to gauging its reputation within the community. One must consider ease of use, backup features, and compatibility with other systems.
Types of Crypto Wallets: Hot vs Cold
The cryptocurrency storage is a diverse landscape with each wallet type catering to specific needs and presenting its own set of advantages and vulnerabilities. At the core of this ecosystem, wallets are primarily differentiated by their connection to the internet. This distinction, often summarized as 'hot' versus 'cold,' fundamentally affects not only how users access and transact with their cryptocurrencies but also the degree of security associated with each method. Grasping the nuances between hot and cold wallets is instrumental for anyone looking to navigate the crypto world safely and efficiently. Let's dive deeper into these categories:
・Hot Wallets: These are wallets connected to the internet. They offer high accessibility, making it easy for users to send and receive crypto on-the-go. Examples include desktop wallets, mobile wallets, and web-based wallets. While their connected nature provides convenience, it also makes them more susceptible to online attacks.
・Cold Wallets: Standing in stark contrast, cold wallets are entirely offline and not connected to the internet. These are considered the safest storage option for long-term holdings. Hardware wallets (like Ledger Nano S or Trezor) and paper wallets are examples. Since they're not exposed to online vulnerabilities, the risk of being hacked is minimal. However, it's essential to keep them physically safe from theft or damage.
Choosing between hot and cold wallets often boils down to a balance between convenience and security with the user's intent and frequency of transactions playing a significant role in the decision-making process.
Cyber Security Tips for Crypto Holders in Australia
In the digital age, where cyber threats constantly evolve and adapt, securing your cryptocurrency assets extends beyond just choosing the right wallet. It's a holistic approach that requires consistent vigilance, understanding of the latest threats, and adapting best practices that cater to one's unique usage patterns. As cybercriminals devise sophisticated techniques to target crypto holders, it becomes even more essential to arm oneself with knowledge and tools that can deter such threats. Here are some pivotal cybersecurity measures every Australian crypto enthusiast should adopt:
・Use Strong, Unique Passwords: It sounds basic, but a strong, unique password can be the first line of defense. Avoid using easily guessable passwords or reusing passwords from other accounts.
・Enable Two-Factor Authentication (2FA): 2FA offers an additional security layer, ensuring that even if your password is compromised, unauthorized users can't access your account without a second verification step.
・Regularly Update Software: Keep your wallet software, apps, and device operating systems updated. Developers regularly release updates to patch vulnerabilities.
・Beware of Phishing Attempts: Always double-check URLs and email senders. Avoid clicking on suspicious links or downloading attachments from unknown sources.
・Use a Dedicated Email for Crypto: Keeping a separate email address exclusively for your crypto dealings can prevent cross-contamination and limit exposure to potential threats.
・Always Double-check Addresses: Before sending funds, ensure the receiving address is correct. Some malware can change copied addresses, rerouting funds to an attacker's wallet.
While the realm of cryptocurrency offers immense potential and freedom, it equally demands users to be vigilant and proactive in maintaining security. Through informed decisions and regular precautions, crypto enthusiasts can enjoy the benefits of digital assets without undue risks. At FameEX exchange, we offer eight distinct security features to safeguard your assets, ranging from anti-phishing codes to 2FA authentication. Our primary goal is to ensure our users' assets remain safe and secure.
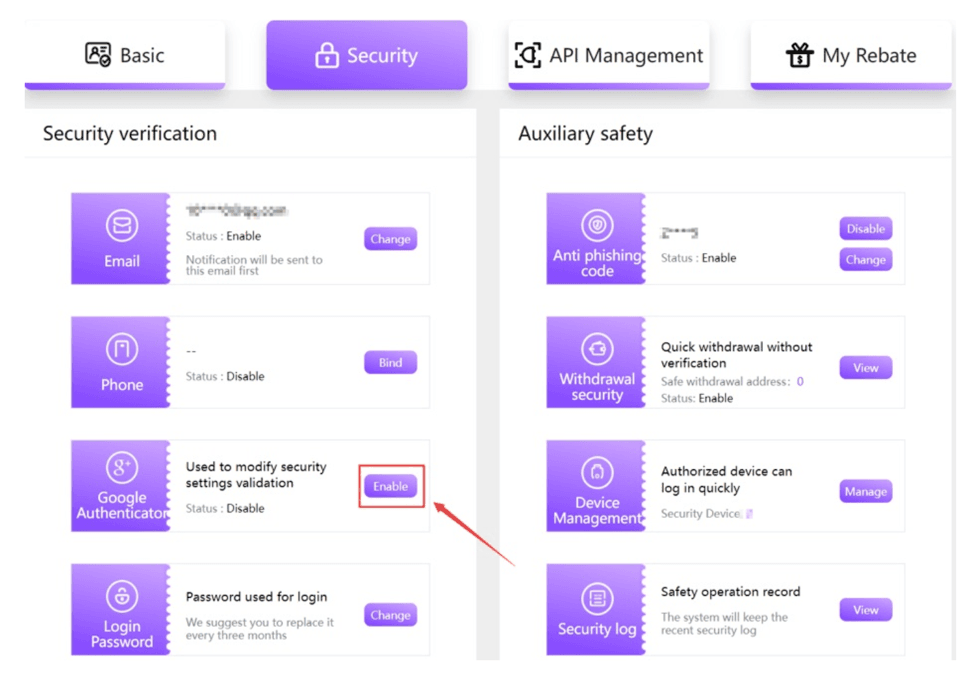
8 different security verification on FameEX
Protecting your Crypto Wallet: Credentials and Authentication
Crypto wallets, akin to personal vaults of the digital realm, are not just about storing cryptocurrencies—they're about ensuring that these assets are inaccessible to malicious actors. The very essence of protection pivots on two vital elements: credentials and authentication. As cyber threats grow in sophistication, so too must the security protocols we employ. Dive in as we elucidate methods to bolster your crypto wallet's defenses to ensure your treasured assets remain untouched and secure. To explore this further, you can refer to our crypto wallets guide or take a look at the different types of crypto wallets and how they work.
Securing your Password and Private Key
A crypto wallet's password and private key serve as the primary line of defense against unauthorized access. When selecting a password, it's crucial to opt for combinations that are both intricate and unique—avoiding easily guessable phrases, like birthdays or common words. As for the private key, this cryptographic signature must be safeguarded with utmost care. It is advisable to store it offline, perhaps written down in a secure location or on a hardware wallet. If this key is exposed or lost, the consequences can be irreversible, with assets potentially lost forever.
Setting up Two-Factor Authentication for Crypto Wallets
Two-Factor Authentication (2FA) has rapidly become a security standard across various online platforms—and for a good reason. Implementing 2FA on your crypto wallet offers an additional layer of security, requiring not only a password but also a unique code typically sent to a personal device, like a mobile phone. This means that even if a malicious actor somehow ascertains your password, they would be halted in their tracks without the second authentication factor. Using apps like Google Authenticator or receiving SMS codes can fortify your wallet's defenses, though hardware-based 2FA solutions might offer even more complicated protection.
Considerations for Secure Crypto Transactions
Beyond just the initial setup and safeguarding of credentials, ensuring security during actual transactions is crucial. Always double-check wallet addresses when sending or receiving funds; a single error or a clipboard hijacking malware could divert your assets to a rogue address. Employ a hardware wallet or cold storage for sizeable amounts, limiting exposure to online threats. Before approving any transaction, thoroughly scrutinize the details, and be wary of phishing attempts which might direct you to faux platforms or apps. Remember, the decentralized nature of cryptocurrencies means that there's often no recourse for misdirected funds, so prudence and caution are your best allies.
Using Secure Exchanges and Trading Platforms
As cryptocurrency and online trading platforms gain traction among Australian seasoned investors and beginners alike, understanding the importance of using secure exchanges and trading platforms becomes vital. These platforms serve as the backbone of online trading, where substantial assets and personal data are constantly at risk. The use of an unsecured platform can lead to irreparable financial loss and breach of sensitive information. Thus, ensuring the safety of these exchanges is not just a recommendation—it's a necessity.
Researching and Selecting Reputable Exchanges in Australia
Before diving into the world of online trading, one must prioritize researching and selecting reputable exchanges. A reputable exchange is not only characterized by its security measures but also by its transparency, user reviews, operational history, and regulatory compliance.
・Transparency: A trustworthy exchange will always be transparent about its operations. This includes fee structures, trading volumes, and any potential conflicts of interest. Many leading exchanges release regular audit reports to prove their financial solvency to their users.
・User Reviews: Just as one would look up reviews before purchasing a product, checking user feedback on an exchange can provide invaluable insights. Positive reviews usually indicate good user experience, whereas recurring negative feedback can be a warning sign.
・Operational History: An exchange's track record speaks volumes. Platforms with a history of security breaches or questionable practices should be approached with caution. On the other hand, exchanges that have been operational for several years without major incidents often demonstrate robust security measures and effective management.
・Regulatory Compliance: It's essential to choose an exchange that complies with the regulations of its operating jurisdiction. Regulatory compliance indicates that the platform adheres to strict standards set by authorities, which often translates to better protection for users in Australia.
The rapid growth of the digital trading domain underscores the need for caution. By carefully researching and selecting reputable exchanges, traders can ensure a safer and more fruitful trading experience. You can clearly see the benchmarks set above that FameEX Exchange strives to meet. FameEX employs a combination of advanced security protocols to ensure the protection of user funds down to the smallest digital unit on the platform. We utilize a multi-layered encryption system, manage private key servers strategically across multiple countries, authorize fund-locking at the node level, and maintain 24/7 system security. This comprehensive approach allows us to offer unparalleled protection for our users' funds.
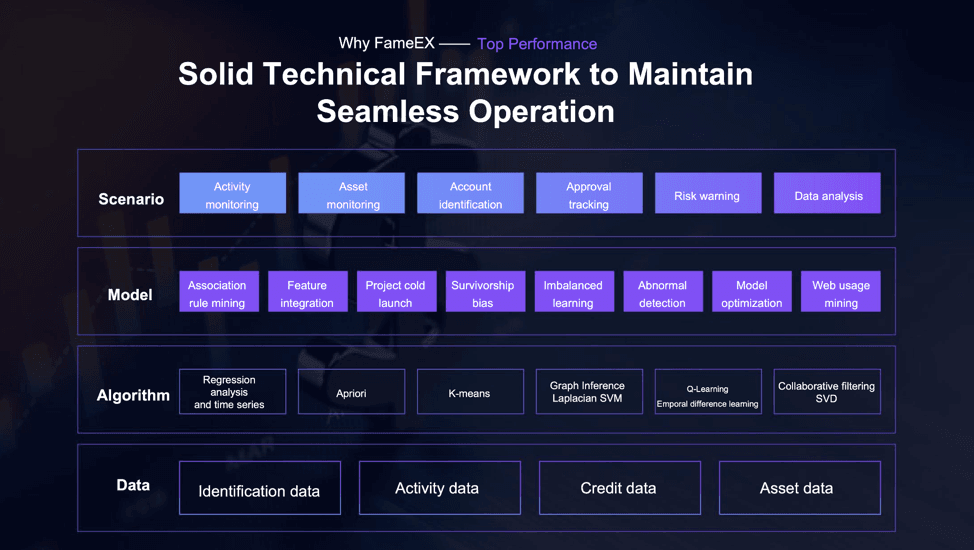
FameEX’s Secure Techincal Framework
Implementing Cold Storage for Long-term Security
As the digital assets' value and popularity continue to soar, so does the target they present to malicious actors. Amidst this threat landscape, cold storage emerges as the gold standard for long-term protection of digital currencies. Unlike "hot" wallets which are constantly connected to the internet, cold storage strategies ensure that your cryptocurrencies remain offline, reducing exposure to online vulnerabilities. But while the concept sounds straightforward, its implementation can be intricate, with a range of methods tailored to suit different needs and levels of technical expertise.
Different Methods of Cold Storage for Cryptocurrencies
As the adage goes, "Not your keys, not your coins." True ownership is determined by the possession and control of the private keys associated with your cryptocurrency. With numerous stories of exchange breaches and malware attacks, many users are shifting their focus to methods that provide maximum security. Cold storage solutions are at the forefront of this shift, offering techniques that keep private keys entirely offline. Whether you're an individual hodler or an institutional investor in Australia, understanding these methods is essential. Let's delve into the various approaches one can adopt for cold storage:
・Paper Wallets: One of the earliest forms of cold storage, a paper wallet is essentially a physical document that contains your private key or a QR code linked to it. This method is immune to online hacks, but one must ensure that the physical document is stored securely and is safe from physical damage or loss.
・Hardware Wallets: These are dedicated devices designed to securely store private keys offline. Popular brands include Ledger and Trezor. They offer a balance between usability and security, requiring a pin to access and a physical action (like pressing a button) to confirm transactions.
・Air-gapped Computers: An air-gapped computer is one that has never been, and will never be, connected to the internet. Cryptocurrency users can generate keys on such a device, ensuring that the private keys are never exposed to an online environment.
・Deep Cold Storage: Used primarily by institutional investors or entities holding large amounts of cryptocurrency, deep cold storage involves creating a private key in a completely offline environment, transferring the cryptocurrency to the associated address, and then ensuring the key remains offline, often stored in high-security vaults or safety deposit boxes.
・Cryptographic "Shards": This method divides a private key into multiple pieces or "shards." These shards need to be combined to access the cryptocurrency. By storing these pieces in separate locations, the risk of theft is reduced since a thief would need to obtain all shards to access the funds.
・Multisig Wallets: While not purely a form of cold storage, multisig (or multi-signature) wallets add an additional layer of security. They require multiple private keys to authorize a transaction. This way, even if one key is compromised, the funds remain secure unless the attacker gains access to the required number of keys.
As with any security measure, each cold storage method has its pros and cons. The right choice depends on individual needs, technical proficiency, and the amount of funds to be stored. However, whatever method one opts for, the guiding principle remains the same: keeping private keys shielded from potential threats to ensure long-term security of one's cryptocurrency assets.
Securing Your Devices and Networks
As cyber threats continue to evolve, and with our increasing reliance on technology for both personal and professional tasks, ensuring the safety and integrity of our digital ecosystems is no longer optional—it's a necessity. From smartphones to corporate servers, every piece of technology we utilize becomes a potential gateway for malicious entities. By understanding the significance of securing our devices and networks, we not only shield ourselves from potential threats but also foster a safer digital environment for everyone.
Updating Software Regularly
One of the most straightforward yet effective measures to enhance the security of your devices is to update software regularly. Software updates, often seen as mere performance enhancers, are crucial defensive mechanisms against potential security breaches. Developers consistently monitor and address vulnerabilities in their applications and systems. When they discover potential flaws, they rectify them through patches and updates. By neglecting these updates, users leave their devices susceptible to exploits that have already been identified and fixed. Therefore, establishing a routine of regular software updates is a proactive step in maintaining the security integrity of your devices.
Using Secure Wi-Fi Networks
In our quest for constant connectivity, we often connect our devices to any available Wi-Fi network. However, not all networks are created equal. Public Wi-Fi, often found in places like cafes, airports, and hotels, can be breeding grounds for cyber threats. Malicious entities can eavesdrop on unsecured networks, capturing personal data and sensitive information. To mitigate this risk, always ensure that you're connecting to encrypted, password-protected networks. When in doubt, consider using a virtual private network (VPN) to encrypt your data and provide an additional layer of protection. Moreover, consistently changing your home and work Wi-Fi passwords and refraining from sharing them unnecessarily can further secure your digital activities.
Beware of Phishing and Social Engineering Attacks
In today's hyper-connected digital landscape, security threats extend far beyond viruses and malware. Phishing and social engineering attacks have emerged as some of the most deceptive and damaging cyber threats. Crafted by malicious actors aiming to deceive, these attacks prey on human psychology, targeting vulnerabilities in judgment rather than software. Whether it's by disguising as a trustworthy entity or manipulating users into divulging confidential information, these sophisticated schemes present a growing challenge to individuals and organizations alike. Recognizing and understanding these threats is the first step to safeguarding against them.
Recognizing Phishing Emails
Phishing emails are deceptive messages designed to trick recipients into divulging personal information, such as login credentials, financial data, or other sensitive details. These emails often replicate the look and feel of legitimate communications from recognized organizations. To recognize a phishing email, look out for:
・Suspicious Sender Addresses: While the name might appear legitimate, the actual email address may contain misspellings or unfamiliar domains.
・Generic Greetings: Phishing attempts often use generic salutations like "Dear Customer" instead of addressing you by name.
・Urgent or Threatening Language: Messages that create a sense of urgency, such as warnings about account suspensions, are classic phishing tactics.
・Mismatched URLs: Hover over any links (but don’t click) to see where they actually lead. If the hyperlink address differs from what's displayed or is unrelated to the supposed sender, it's likely a scam.
・Unexpected Attachments: Unsolicited emails with attachments should be a red flag, as they might contain malware.
・Request for Personal Information: Legitimate entities will rarely, if ever, ask for sensitive information through email.
At FameEX, we recommend setting up an anti-phishing code to authenticate emails from our official platform. This will help you distinguish between genuine FameEX communications and potential scams. Once you activate the anti-phishing code, all emails from FameEX will include it. Refer to this guide to learn more about the setup process.
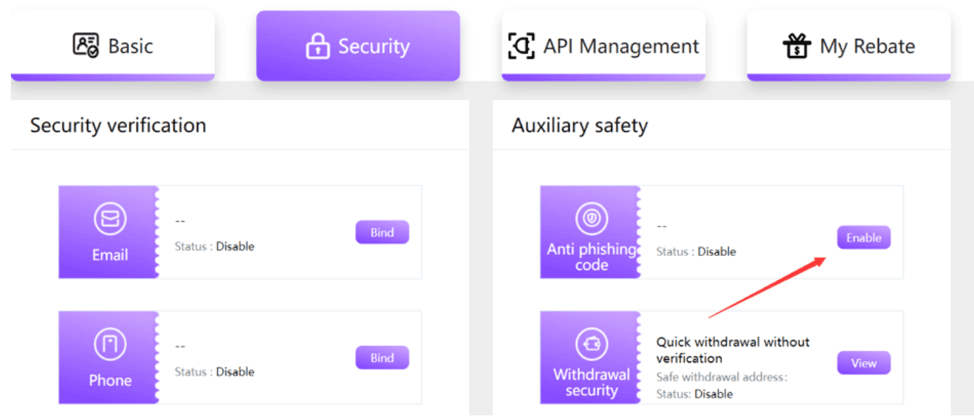
Enable your anti-phishing code
Verifying the Authenticity of Websites
Before entering any personal or financial information on a website, it's crucial to ensure its authenticity. Here's how you can verify:Check the URL: Ensure the website address starts with "https://" where 's' indicates a secure connection. Additionally, watch for subtle misspellings or additional characters that could indicate a fake website.
・Look for the Padlock Icon: Most browsers display a padlock symbol in the address bar for secure sites, indicating an SSL certificate.
・Examine the Site’s Content: Legitimate websites will be free from glaring grammatical errors, high-quality graphics, and a professional layout.
・Verify Through External Sources: If in doubt, consult third-party sources like online reviews or customer feedback on other platforms.
・Use Website Verification Tools: Tools like Google's Safe Browsing can help determine if a website has been reported for phishing or malicious content.
・Double-Check Domain Registration: Look up the website on domain registration databases, like WHOIS, to verify its registration details and legitimacy.
Always trust your instincts. If something feels off or too good to be true, it's essential to take a step back and verify before proceeding.
Conclusion
As the digital frontier expands, so does the range of threats targeting unsuspecting participants. By adopting possible security practices like using hardware wallets, enabling two-factor authentication, and staying informed about the latest scams, new investors can drastically reduce their vulnerability. It's imperative to treat your digital assets with the same, if not more, caution as traditional finances. After all, in the decentralized universe of crypto, being one's own bank means being one's own best line of defense. Safeguarding your investments is not just about preserving monetary value, but about maintaining trust in a system that promises to redefine the future of finance.
FAQ About Crypto Security Tips
Q: What Are Some Essential Security Tips for New Cryptocurrency Investors?
A: Ensure your crypto safe practices include using strong passwords, employing two-factor authentication, and utilizing cold wallets.
Q: What Are Some Tips for Preventing Crypto Theft?
A: Avoid public Wi-Fi, be wary of phishing scams, use hardware wallets, and keep your software updated.
Q: How Can I Improve My Crypto Security?
A: By using a combination of cold storage, unique passwords, avoiding crypto scams on social media, and staying updated on common crypto threats.
The information on this website is for general information only. It should not be taken as constituting professional advice from FameEX.