Secure Storage Solutions: Best Practices for Safeguarding Your Private Keys
2024-01-23 04:00:40The rapid expansion and widespread popularity of cryptocurrencies have heightened the demand for secure and reliable ways to handle digital assets. The frequent news in Australia of major cryptocurrency breaches has left many new to the blockchain world questioning the best practices for safely storing private keys. At the core of this issue is the proper safeguarding and management of private keys, which are essential for accessing and managing cryptocurrency holdings. By effectively managing these keys, you can prevent the loss of your valuable digital assets due to hacking, theft, or even human mistakes. Our detailed guide will show you the steps to safely store private keys, covering everything from basic methods to more sophisticated security strategies.
Understanding Private Keys
Private keys emerged as a fundamental concept in Australia, integral to various cryptographic systems including those used in cryptocurrency and secure communications. A private key, in essence, is a secret alphanumeric code that grants an individual exclusive access to their digital assets or encrypted messages. Primarily, private keys are used in tandem with public keys to form a secure cryptographic pair. This pair operates on the principles of asymmetric encryption, where the public key is freely shared and used for encryption, while the private key remains confidential and is used for decryption. Understanding this relationship is crucial for comprehending how private keys facilitate secure digital transactions and communication. Moreover, the security and management of private keys are paramount. The loss or compromise of a private key can lead to irreversible consequences, including the loss of digital currencies or the breach of confidential communications. If you're interested in understanding the differences between a private key and a public key, you can refer to this guide.
Best Practice for Australians: How to Store Private Keys Securely?
Protecting private keys is essential in the digital era now, especially for those who engage in cryptocurrency transactions or manage digital assets. Alongside adhering to the recommended methods for safekeeping private keys, you can adopt additional sophisticated security strategies to increase the safeguarding of your cryptocurrency assets. These strategies are designed to reduce the chances of unauthorized access and bolster the security framework surrounding your private keys.
1. Create Strong and Unique Passwords for Your Wallets
Strong and unique passwords act as the first line of defense for your digital wallets. A robust password should be a complex combination of uppercase and lowercase letters, numbers, and special symbols. Avoid using easily guessable information like birthdays or common words. Each wallet you own should have a distinct password to prevent a single breach from compromising all your assets. Regularly updating these passwords and using different ones for each login can significantly enhance security.
2. Use Two-Factor Authentication (2FA)
Two-factor authentication (2FA) provides an additional security layer beyond just the password. With 2FA, accessing your wallet requires something you know (your password) and something you have (like a mobile device that receives a unique code). This method drastically reduces the risk of unauthorized access, as an attacker would need both your password and your second authentication factor.
3. Regularly Backup Wallet Data and Store Backups Securely
Frequent backups of your wallet data are vital for recovery in case of device failure, loss, or theft. It's crucial to store these backups in multiple secure locations, away from your primary device. Consider using physical storage like USB drives or external hard drives, and keep these in locked, secure environments like a safe. Cloud storage can also be used, provided it's encrypted and protected with strong passwords and 2FA.
Hardware wallets or USB drives, which are secure and offline, are created for the sole purpose of safeguarding private keys. They utilize dedicated hardware for key management, including hardware keys like FIDO2 and trusted platform modules (TPMs). These specialized devices provide robust encryption and security capabilities, drastically reducing the likelihood of unauthorized access, tampering, or extraction of keys. By incorporating these devices into your key management plan, you can substantially increase the security of your private keys.
4. Encrypt Backups
Encrypting your backups adds an essential security layer, making the data inaccessible to anyone who doesn't have the encryption key. Use strong encryption methods and keep the encryption keys separate from the backups themselves, ideally in a different secure location.
5. Secure Physical Access to Your Wallets and Backup Locations
Securing physical access to your devices and backup locations is as crucial as digital security especially in Australia. Ensure that any device or location that stores your wallet information or backups is well-protected. This could involve physical locks, security systems, or simply choosing discreet, safe locations for storage.
6. Protect Your Devices Against Malware and Phishing Attacks
Your devices are often the gateways to your digital wallets. Protect them with updated anti-virus and anti-malware software. Be vigilant against phishing attempts - fraudulent efforts to trick you into revealing sensitive information like your private keys. Always verify the source of messages and emails, especially those requesting personal information or urging immediate action.
7. Avoid Using Public Wi-Fi and Devices for Wallet Management
Public Wi-Fi networks in Australia and shared devices are vulnerable to security breaches. These networks can be easily intercepted by cybercriminals. Always manage your wallet transactions on a secure, private network and use devices that you trust and control. If you need to access your wallet on the go, consider using a VPN for added security.
8. Keep Your Wallet Software and Security Tools up to Date
Software developers regularly release updates that patch security vulnerabilities. By keeping your wallet software and any associated security tools up to date, you can protect against the latest threats. This includes not just your wallet software, but also the operating systems of your devices and any other related applications.
9. Keep Your Wallet’s Secret Recovery Phrase Offline
Your wallet's secret recovery phrase is a critical backup tool for accessing your assets if your device is lost or fails. This phrase should be kept offline at all times, ideally written down on paper or stored on a physical medium in a secure location. Never store your recovery phrase on an internet-connected device.
10. Encrypt Your Computer’s Hard Drive
Encrypting your computer’s hard drive adds a significant barrier against unauthorized access. Should your computer be lost or stolen, encryption ensures that the data stored on it, including any wallet information, remains secure and inaccessible without the encryption key.
11. Use Password Managers
Password managers are tools that securely store and manage your passwords. They allow you to use complex, unique passwords for each of your accounts, including your wallets, without the need to remember each one. Ensure that your password manager is reputable and protected by a strong master password. Modern password managers offer secure storage for a variety of sensitive information, including passwords and private keys. It's important to select a password manager that is reputable and known for its high level of security.
12. Be Cautious With the Wallet Software
When selecting wallet software, opt for reputable, well-reviewed options. Be wary of new or unverified software, as these can sometimes be fronts for scams or malware. Always download wallet software from official and verified sources to avoid counterfeit applications.
By following these best practices, you can significantly enhance the security of your private keys and protect your digital assets against a wide range of potential threats.
What if I Lose My Private Key?
The private key is a critical component of wallet ownership, acting as the definitive proof of your control over a wallet address. Unlike traditional banking systems, most digital and cryptographic systems do not have a central authority to reset or recover lost keys. This irreversible loss highlights the necessity of robust backup and recovery strategies. It's essential to keep this key strictly confidential and never reveal it to anyone, either online or offline. Exposure of your private key can lead to the loss of your funds. For safekeeping, it's advised to store the key in a secure location, ideally offline, like on a piece of paper, accessible only to you. Remember, if you lose your private key, there's no method to retrieve or recreate it.
Besides the private key, there are alternative methods for importing your wallet address and recovering the tokens contained within. These methods include:
・Mnemonic Phrase/Seed Phrase/Recovery Phrase: One of the primary recovery methods is the utilization of a recovery phrase or seed phrase. This is a series of words generated at the creation of a wallet, which can be used to regenerate private keys. This is a sequence of 12 or 24 randomly chosen words, and sometimes 13 or 25 words, with the additional word functioning as a personally set password. However, this method is only effective if the recovery phrase has been securely backed up and is accessible.
In cases where recovery phrases are not available, the options are significantly limited. Some advanced cryptographic systems may offer alternative recovery methods, but these are not universally available and often come with their own security trade-offs.
・Keystore/JSON File: This is a file containing an encrypted version of your wallet's private key. Typically, these are provided by your wallet service provider when you create a wallet address. They usually emphasize the importance of backing up these details in a secure, personal location. If you have access to any of these, you can easily access or import your wallet address. However, without any of these three, regaining access to your wallet address and recovering your tokens may be impossible.
In cases where recovery phrases are not available, the options are significantly limited. Some advanced cryptographic systems may offer alternative recovery methods, but these are not universally available and often come with their own security trade-offs.
・Keystore/JSON File: This is a file containing an encrypted version of your wallet's private key. Typically, these are provided by your wallet service provider when you create a wallet address. They usually emphasize the importance of backing up these details in a secure, personal location. If you have access to any of these, you can easily access or import your wallet address. However, without any of these three, regaining access to your wallet address and recovering your tokens may be impossible.
While the loss of a private key can have severe consequences, understanding the available recovery options and implementing preventive measures can significantly mitigate these risks.
What Are the Risks of Insecurely Storing Cryptocurrency Private Keys?
Insecure storage of private keys opens a myriad of vulnerabilities, the most significant being the risk of theft. Cybercriminals continuously evolve their tactics and tools to exploit weak security measures around private keys. Once obtained, these keys give attackers complete access to the associated cryptocurrency funds, leading to direct financial losses.
Another major risk is the accidental loss or exposure of private keys due to inadequate security practices. This can occur through data breaches, physical theft of devices where keys are stored, or even through simple mishaps like misplacing a paper wallet or hardware device. Such losses are often irreversible, as cryptocurrencies operate on decentralized networks without a central authority for dispute resolution or recovery.
Transactions conducted over these networks can be intercepted, providing another avenue for malicious actors to access private keys. Additionally, the threat of malware and phishing attacks specifically designed to target digital wallets and extract private keys is a growing concern. Without proper measures, private keys can become inaccessible in the event of the owner’s incapacity or death, leading to the permanent loss of digital assets for heirs or beneficiaries. By understanding these risks, users can take proactive steps to ensure the safekeeping of their digital assets, fortifying their defenses against potential threats in the ever-evolving landscape of cryptocurrency security.
How Can I Protect My Cryptocurrency From FameEX?
If you want to protect your cryptocurrency on FameEX, we offer 8 different verification methods for our Australian users. These range from login verification through email and mobile phone to Google authentication. These steps and features help keep your login access secure. Additionally, we provide auxiliary safety measures such as anti-phishing code setup, enhanced withdrawal security, device management, and a security log. These measures offer further protection to ensure the safety of your account. They are particularly effective against cyber security threats like email attacks. Make sure to manage your device and regularly check the security log for any unusual activities.
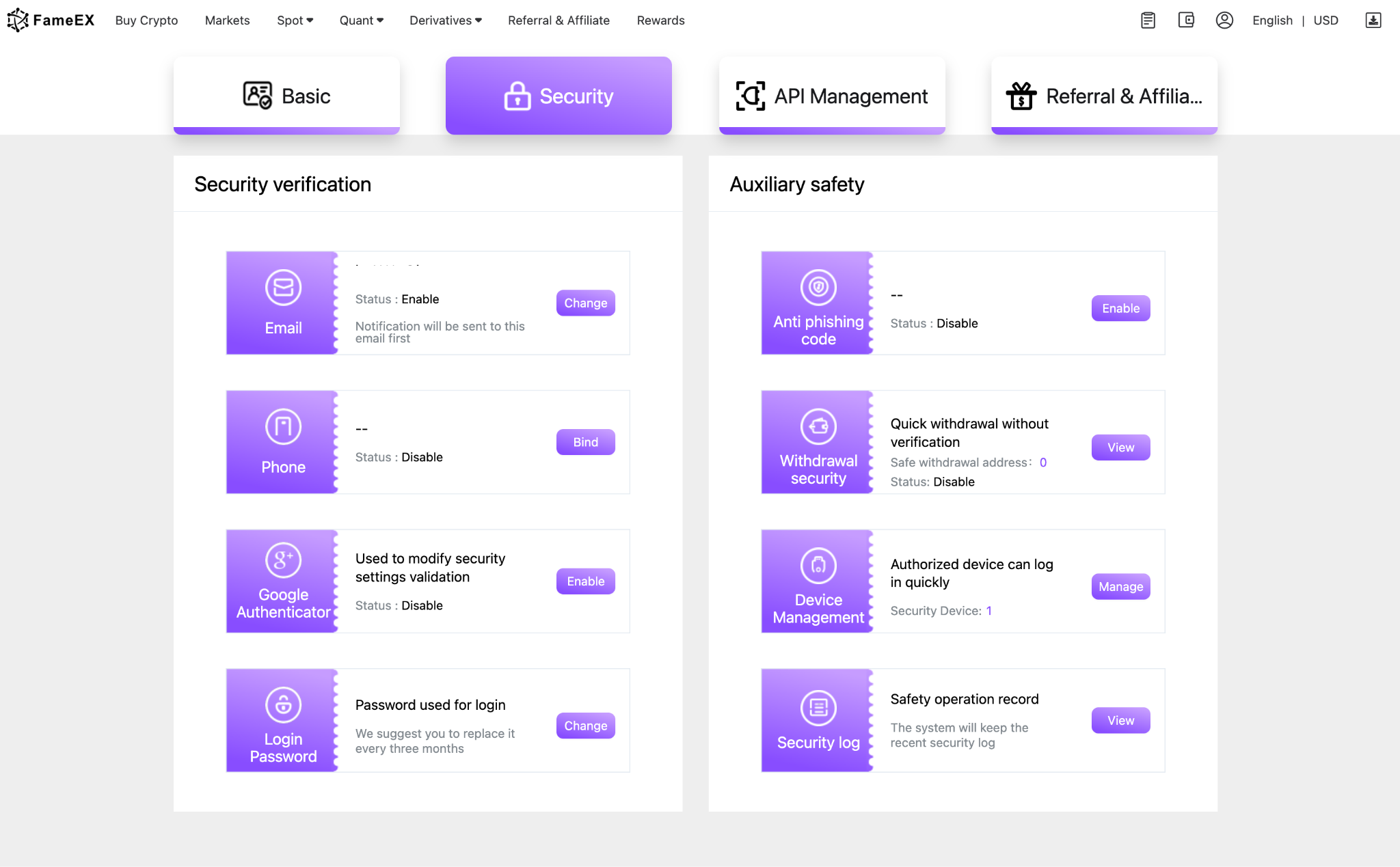
Is It Safe to Store Private Keys on FameEX?
FameEX, like many cryptocurrency exchanges and platforms, offers a range of security features designed to protect user accounts and assets. However, the inherent risks associated with online platforms must be carefully considered. FameEX offers a highly secure environment for storing private keys, thanks to its comprehensive Four-Layer Technology Protection. This multi-faceted approach to fund security encompasses the following features:
・Four-Layer Encryption Method: FameEX's advanced encryption safeguards every aspect of fund storage, including on-chain and off-chain security, effectively neutralizing any technical threats.
・Split Storage in Cold and Hot Wallets: The platform employs a dual wallet system, separating funds into hot (online) and cold (offline) wallets. This division enhances security by isolating the majority of funds from online threats. Additionally, private keys are randomly split, encrypted, and stored separately, bolstering protection against unauthorized access.
・Asymmetric Encryption with One-Way Hash Function: This innovative approach generates a unique private key for each public key using a one-way hash function. The irreversible nature of this process ensures that matching the private key with its corresponding public key is the only way to access on-chain funds, making them virtually indecipherable on FameEX.
・Decentralized Encrypted Management of Wallet Storage: Embracing a decentralized approach, FameEX secures the storage of private keys with symmetric encryption. It further enhances security by implementing multiple permission layers for database access, thus controlling and securing wallet privacy effectively.
・Tamper-Proof Full-Node Wallet: The adoption of a full-node wallet system, which synchronizes all block data, ensures the integrity and security of stored data. This approach guarantees that the data remains tamper-proof, providing both users and the platform with a high level of fund security.
FameEX's robust and layered security measures provide a safe and secure environment for storing private keys, giving users peace of mind regarding the safety of their funds. Moreover, the security of private keys on FameEX is also assessed in terms of user account security features. This includes two-factor authentication (2FA), email and SMS alerts, and other account-level security measures that the platform provides to safeguard user accounts from unauthorized access.
FameEX employs robust methods to ensure the security of private keys, leveraging global and hierarchical management strategies. The company's R&D teams are distributed across various countries, each focusing on the encryption of private keys for different pairings. This global spread enhances fund security through geographical and operational separation, with the operational teams and private key servers located in South Asia and the Americas. This setup isolates R&D, permissions, funds, and servers, reducing the risk of security breaches. Additionally, FameEX adopts a hierarchical management model, where code compilation rights are supervised by multiple technical directors using a layered approach. This strategy maintains the independence of codes from different departments and ensures clear authority directives. By preventing internal conflicts and minimizing financial risks, this method strengthens the overall stability and efficiency of the platform's operations.
The trade-offs between convenience and security are critically analyzed to provide users with a comprehensive understanding of the best practices in private key storage. It is particularly valuable for individuals and entities involved in cryptocurrency trading and investment, providing them with essential insights into the safety measures employed by FameEX and guiding them in making informed decisions regarding the storage and management of their private keys.
The information on this website is for general information only. It should not be taken as constituting professional advice from FameEX.